With the advancement of smart factories using digital data, one of the concerns is security measures. Personal computers are protected by installing security software, but how is security maintained at a factory?
Recently, there has been much news regarding the serious security damage of factories. Most of the time, ransomware, which are viruses that require money for ransom, can be installed via a network or USB. This is caused by a malicious program that locks an infected PC or encrypts files so that the infected PC cannot be used and then demands a “ransom” in exchange for its return. If infected, operation of the PC becomes impossible and work is halted. The files of the PC are encrypted and unavailable, or if you pay a ransom, financial damage is accrued.
Until now, factories have blocked access from the outside to the edge layer, where large amounts of data are generated. However, IoT has increased the importance of external data collaboration, such as bringing data to the cloud layer, sharing data among multiple locations, and externally monitoring the status of production lines. However, this has led to an increase in attacks that take advantage of equipment vulnerabilities, and there have been frequent incidents of shutdowns and lower productivity due to uncontrolled equipment, resulting in the loss of billions of dollars.
One of the structural causes of unauthorized access is that the ICT department of the manufacturer is not familiar with the network and telecommunication environment of the manufacturing site and cannot comprehensively monitor data security. Manufacturing sites face unique environmental challenges, such as 1) systems that should not affect existing equipment, 2) a large number of old devices that cannot be updated, and 3) the necessity of devices maintenance such as USB devices, but these issues have not been coordinated with ICT departments.
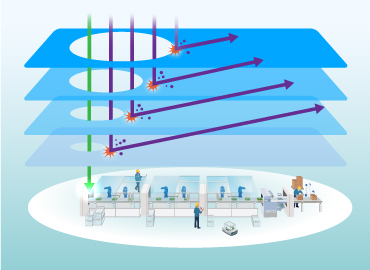
To solve this problem, multiple methods to prevent the spread of infection and damage are usually used as security measures in factories. Specifically, by applying multiple filters, such as DoS attack protection, IP address communication control by firewalls, protocol filters, and vulnerability attack detection / blocking by IPS to devices such as PCs, servers, controllers, and USBs and points connecting them, we will build security devices that only allow access through normal communication to prevent unauthorized access. This filter-based approach eliminates the need for strong point-specific defenses and allows for increased security without changing the network settings of existing facilities.
i3-Mechatronics, a factory automation and digital data solution promoted by Yaskawa, has been verified through product validation in cooperation with partners who are well versed in security software, and it has been confirmed that the i³-Mechatronics works properly even with controllers, servo packs, and other devices under specific environments.